To make a Secure Conference with Silentel, the user simply selects multiple users from the Silentel contact list. Selected users will receive notification similar to an incoming call. Users will be connected to a conference call after accepting incoming notification.
Other users can be added during the conference itself.
The user can leave the conference at any time and then rejoin it again.
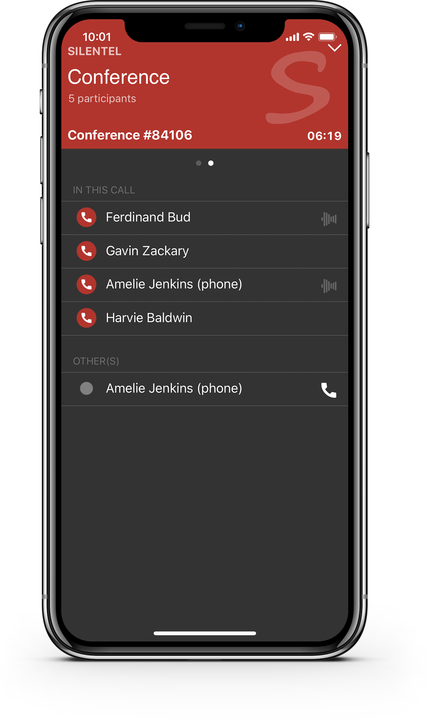
The conference allows you to view the list of participants with the following details:
- Who received a conference call (or who was invited but did not accept a conference call)
- Who is currently talking
How is Secure Conference encrypted?
Most conference systems which declare encrypted communication did not provide true end-to-end encryption.
How other systems works? Encrypted communication is established between user and conference server. User's voice stream is encrypted and sent to server. Server decrypts the voice streams received from users and mix it together. Mixed voice stream is encrypted and forwarded to users. And this is wrong, because the conference server is the weak point where the encrypted communication can be intercepted or compromised in several ways.
How Silentel Secure Conference works? Each Secure Conference communication is protected by a unique encryption key which is distributed solely between participants. Voice stream is encrypted before sending and is decrypted only after delivery to receivers (directly in users' devices). Voice stream is mixed directly on users' devices (not by the server or any other part of the system). Data are never decrypted during transfer. Even the Silentel Server never knows the encryption keys and is not able to decrypt the content of Secure Conference communication.

