More than 10 years of proven security, regular independent certifications from several NATO countries combined with military-grade encryption makes your information secure at all times.
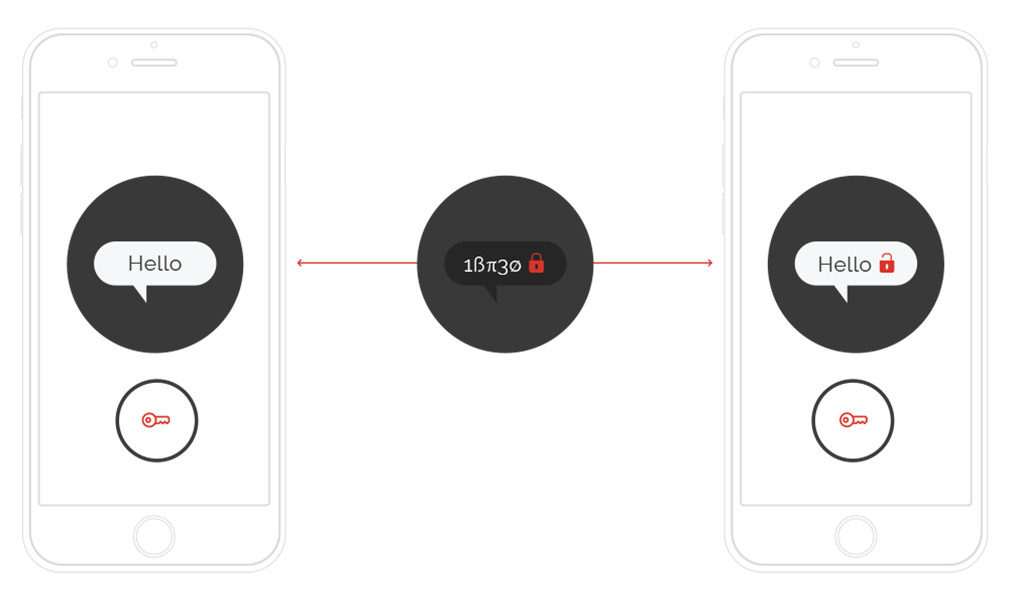
Communication data are encrypted before sending and are decrypted only after delivery to receiver (directly in users' devices). Data are never decrypted during transfer. Even the Silentel Server never knows the encryption keys and is not able to decrypt the content.
Each communication is protected by a unique encryption key which is generated during communication establishment. It means that each communication between two users, even each communication between the same two users, has its unique encryption keys, which cannot be predicted. Each encryption key is destroyed immediately after communication ends.
No information remains being stored on the user's device, not even the contact list. Even when a mobile device is lost or stolen, no Silentel information will ever be available to anybody finding the device. This means that no forensic analysis will retrieve any sensitive information (like voice calls, text messages, files and contacts) from the user's device.
The telco operators are storing a huge number of personal meta data about the subscribers, their communication and location. The Silentel system doesn't require any personal data (name, address, GSM number, location or anything else). Communication is transmitted only as data (similar to browsing on internet) in encrypted form what makes your calls and messages non-traceable.
Silentel is the first solution world-wide for secure mobile communication that was positioned in the NATO Information Assurance Products Catalogue (NIAPC). NIAPC brings together all INFOSEC and IA products that are evaluated and suitable for use in the NATO environment (NATO nations and NATO civil and military bodies).
Since 2006, Silentel is certified by a growing number of National Security Agencies as a product for secure mobile communication up to levels RESTRICTED and CONFIDENTIAL.
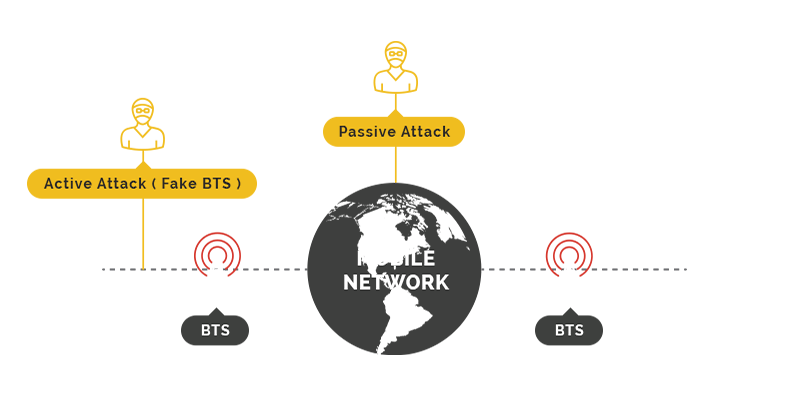
Design weaknesses in the GSM standard allows using fake mobile towers between the target mobile phone and the real towers. There're many demonstrations and manuals on how to perform such attacks based on open-source software and commonly available hardware at the price of a few thousand euros.
Did you know that GSM signal is always encrypted? Unfortunately, encryption is so outdated and weak that there exist several techniques that enable decrypting your communication with 99% success rate.
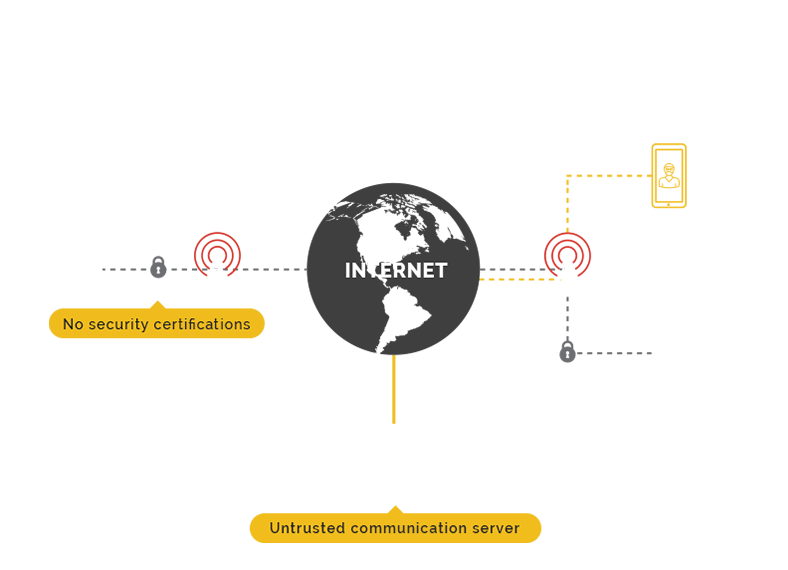
The first and most important factor to consider regarding security is if a third-party security evaluation is available. Without this the supplier can claim any kind of security mechanism since there is no way the client can verify or prove the contrary.
Most encryption applications use a central communication server. Claims that the application use end-to-end encryption is useless when the communication server is able to intercept or reconstruct the session encryption key or can force to re-encrypt the message.
Most encryption applications allow open registration. In this case – How can you control your communication group? How can you be sure about the identity of your contacts? How can you avoid sending messages to someone with fake identity by accident?
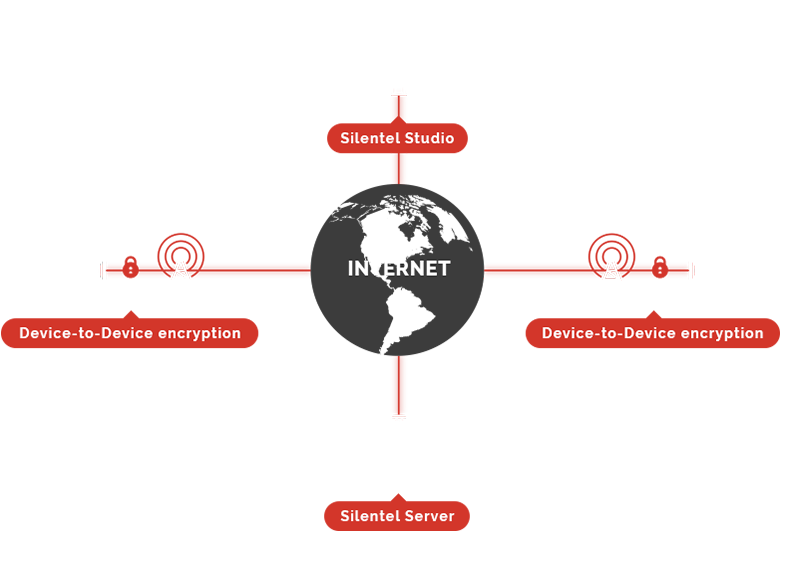
a smarter and simpler way to manage your users and closed communication groups.
Learn Morenever knows the encryption keys and is not able to decrypt any content.